Almost three quarters (71%) of U.S. banking customers prefer to manage their bank accounts through a mobile app or computer, according to the American Bankers Association.
As a doctor, digital banking can be a great tool for conveniently monitoring and managing your money from anywhere at any time (like at 3 a.m. at the hospital during an overnight shift), but it’s crucial to keep your finances and personal information safe as you access your accounts.
Here are 10 basic rules to use as you bank from a mobile device or computer.
10 tips for online banking security
1. Use strong passwords
Your password is an essential line of defense in protecting your money and your personal information. Create a strong password by:
- Choosing longer passwords, ideally 12+ characters
- Using a mix of letters (both uppercase and lowercase), numbers, and symbols
- Avoiding common words and guessable information like birthdays or simple words—experts recommend a phrase that you can remember such as “iM@tch3dT0d@y!”
- Using unique passwords for different accounts
2. Enable two-factor authentication (2FA)
Two-factor authentication offers an extra layer of security; it requires a second form of identification, such as a text message or email code or authenticator app, like Google Authenticator or Microsoft Authenticator.
If your bank doesn’t already require 2FA, ask your bank if they offer it and how to enable it.
3. Keep your software updated
Regularly updating your device’s operating system, web browsers, and mobile apps can help protect against security vulnerabilities. Additionally, installing and maintaining antivirus software can help protect against malware and viruses.
4. Avoid unsecured public WiFi
Public WiFi can be vulnerable to hackers. When banking, use private, password-protected WiFi to access your bank accounts.
Here are security tips:
- Verify the network. Before connecting, confirm that the network name is legitimate, especially in places like cafes or airports. Fake WiFi networks are often set up to trick users into connecting and stealing their information.
- Use a Virtual Private Network (VPN). A VPN encrypts your internet connection, making it much harder for hackers to intercept your data. Always use a reliable VPN service when accessing sensitive information over public WiFi.
- Use secure websites. Ensure that the website URL begins with “https://” and displays a padlock icon in the address bar. This indicates that the site is secure and encrypts data.
5. Be aware of phishing scams
Scammers use phishing to trick victims into revealing sensitive information through emails, text messages, and phone calls. Phishing scams may look like:
- A link to make a payment
- An invoice you don’t recognize
- A problem with your account or payment information
- A need to confirm personal or financial information
- A coupon for free products or services
- A notification of suspicious activity or log-in attempts
These messages often look official, but they’re not. Here are some clues that a message may be a scam:
- It has a generic greeting that doesn’t mention your name or any other identifying information.
- It has spelling or grammar errors. (Although some phishing emails are getting more sophisticated so don’t rely on this tip alone.)
- It creates a sense of urgency or fear to prompt immediate action.
Here are some tips for dealing with potential phishing scams:
- Be skeptical. Approach unsolicited emails, texts, and calls that ask for personal information with caution. Verify the authenticity of the communication by contacting the company through official channels, like the phone number, email address, or chat feature found on their website.
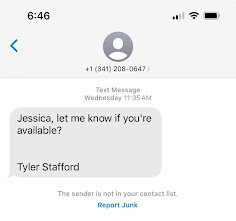
A newish scheme is to text new employees pretending to be the president or CEO asking for a favor or if they can help with something. Always verify the phone number before proceeding.
- Check the email address. Hover over the sender’s email address to check the actual domain. Phishing emails often use addresses that mimic legitimate domains but may contain extra characters or misspellings (@panaceafinancial.com – legitimate; @panceafinancial.com – fake).
- Avoid clicking links. Hover over links in emails or messages to see the URL before clicking. If it looks suspicious or doesn’t match the expected domain, don’t click it. Instead of clicking on links, manually type the company’s URL into your browser’s address bar.
6. Monitor your accounts
Regularly review your bank statements and transaction history for any unauthorized activities. Use your bank’s alert system to notify you of unusual account activity. You can set up alerts for:
- High or low balances
- Password changes
- Personal information updates
- New transactions
- Failed login attempts
7. Access your account smartly
Only download banking apps from trusted sources like the Apple App Store or Google Play Store. Access your bank’s website by typing the URL directly into your browser, rather than clicking on links in emails or messages.
8. Logout after each session
Especially when using shared or public devices, always logout once you are finished with your online banking session.
9. Secure your devices
Use strong passwords or PINs on your phone or computer to avoid the risk of someone accessing your accounts through your device. ALWAYS have a pin or password on your phone and laptop.
10. Be cautious with automatic logins
Avoid saving passwords in your browser or using automatic login features, especially on shared or public devices.
Is online banking safe?
Online banking is a safe way to manage your finances, but it is important to protect your information and money by following proper security measures. Use these 10 tips to enjoy the convenience of online banking with greater peace of mind.
If you ever have any concerns about communications that look like they came from Panacea Financial, contact us via phone, email, chat, or form submission here.








